CYBER SECURITY: Are You Cyber Safe?
While there is no silver bullet and no one solution to cyber safety, layered defenses are best practices and rely on multiple measures to detect and protect against cyber dangers.
- “Parasitic malware feasts on critical infrastructure”
- “Digital vigilantes weaponize vulnerability disclosure”
- “Rushed digital transformation destroys trust”
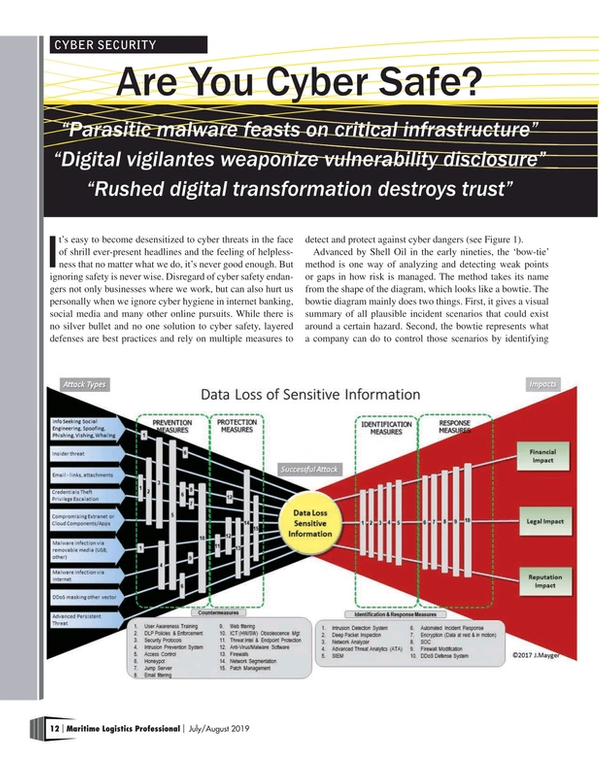
It’s easy to become desensitized to cyber threats in the face of shrill ever-present headlines and the feeling of helplessness that no matter what we do, it’s never good enough. But ignoring safety is never wise. Disregard of cyber safety endangers not only businesses where we work, but can also hurt us personally when we ignore cyber hygiene in internet banking, social media and many other online pursuits. While there is no silver bullet and no one solution to cyber safety, layered defenses are best practices and rely on multiple measures to detect and protect against cyber dangers (see Figure 1).
Advanced by Shell Oil in the early nineties, the ‘bow-tie’ method is one way of analyzing and detecting weak points or gaps in how risk is managed. The method takes its name from the shape of the diagram, which looks like a bowtie. The bowtie diagram mainly does two things. First, it gives a visual summary of all plausible incident scenarios that could exist around a certain hazard. Second, the bowtie represents what a company can do to control those scenarios by identifying tripwires or safety barriers. By applying the bowtie to cyber risks, we can visualize their impact and mitigating activities, creating a clear differentiation between proactive and reactive risk management.
The starting point of any bowtie analysis is the hazard, that which has potential to do damage, a successful attack. A successful cyberattack results in an event (represented by the center), and in this case, the event is data loss of sensitive information. Threats (on the left) are whatever will cause the event. Consequences are to the right, the result of the event (the impact). In the case of sensitive data loss, there may be financial, legal or reputational impact or all three. Prevention and protection measures (safety barriers) can prevent a successful attack. If the attack bypasses the countermeasures and there is a successful attack, identification and response measures are critical in mitigating the impact of a successful attack.
All cybersecurity risks and events can be illustrated by four bowtie analyses. These include:
- Data loss of sensitive information;
- Malicious software infection;
- Distributed denial of service (DDoS); and
- Physical Information & communication technology (ICT) perimeter intrusion & unauthorized access to ICT equipment.
Since best practices for information security involve layered defenses, security programs should deploy multiple prevention, protection, identification, and response measures. These best practices are relevant to any network environment such as process control networks, industrial control systems or corporate networks. One very necessary measure is the establishment of a Security Operations Center (SOC), which monitors, detects, investigates, and responds to cyberattacks, around the clock. A SOC for 10,000 employees costs about USD $1 million annually. But among all the defensive measures, a SOC lowers the risk exposure from cyberattacks the most.
Another necessary measure, Security Awareness Training is critically important because one-third of cyber breaches are caused by employees/insiders.
Cybersecurity budgets vary depending on the industry and risk. Defense companies are high on risk because of nation-state spying. Utilities supporting critical infrastructure have elevated risk profiles as well. Banks tend to spend more than construction companies, but the average annual cybersecurity budget across all industries is approximately one-quarter of one percent of revenues. For instance, a USD 3 billion dollar industrial company should target approximately USD $8 million yearly on cybersecurity.
Privacy concerns and breaches have resulted in the European General Data Protection Requirement (GDPR). The California Consumer Privacy Act (CCPA) takes effect on January 1, 2020. Both regulations have far-reaching tentacles and teeth. Non-compliance with GDPR can result in fines up to 20 million Euro or 4 percent of annual global revenue, whichever is higher. CCPA will levy fines of USD $7,500 per violation if the business does not cure the violation within 30 days of being notified. An effective security program is a necessity for multiple reasons including good governance and, to be sure, no company wants to be in the cross-hairs of regulators.
An experienced security practitioner can frame security in terms of risk, the language of executive management. While the amount of security (and budget) depends on the company’s risk appetite, insufficient security elevates risk. The migration of applications to AWS or Azure adds a new layer of complexity. A cybersecurity consultant can help companies meet their security needs including cloud app security, network security architecture, governance and regulatory compliance, business continuity planning, assessments and audits, or augmenting staff to close temporary skill shortages to name a few.
It used to be death and taxes were the only certainty. Today it’s also about getting hacked. English author Aldous Huxley said that cynical realism is the intelligent man’s best excuse for doing nothing in an intolerable situation. Doing nothing is not an option in cybersecurity.
Jeffery Mayger provides cyber security advisory services at Concord, a consultancy for information technology integration and security services. His cybersecurity background includes Chief Information Security Officer (CISO) for global mining company Sibelco and information security services to upstream oil/gas customers. In addition to his B.S in Mechanical Engineering, Mr. Mayger also holds a Master of Business Administration (MBA) from the University of Texas. His Information Security background includes designations as Certified Information Security Professional (CISSP) and Certified SCADA Security Architect (CSSA). Mr. Mayger can be contacted at [email protected].
This article first appeared in the JULY/AUG print edition of Maritime Logistics Professional magazine.
Read CYBER SECURITY: Are You Cyber Safe? in Pdf, Flash or Html5 edition of Jul/Aug 2019 Maritime Logistics Professional
Other stories from Jul/Aug 2019 issue
Content
- CYBER SECURITY: Are You Cyber Safe? page: 12
- Trust and Independence: page: 14
- PORT PROFILE: Big Baltimore page: 22
- BREAKBULK SHIPPING: Breakbulk Breaks the Mold page: 28
- New ‘Eyes’ on the Prize page: 34
- Transforming Today’s Transportation Terminal for Tomorrow’s Technology page: 44